This article aims to better understand how a hacker can hack our Hotmail / Outlook / Live account , to guard against it properly. We will also talk about a flaw that is now corrected that shows that an implementation error can have disastrous consequences and allow us to draw conclusions about the security of our accounts.
I remind you that this site is not intended to help to hack but to understand the attacks to defend itself .
How could a hacker so easily hack a Hotmail account?
Example with the use of a flaw in Hotmail:
This flaw is now fixed . We will dissect it to better understand what may have happened if you have been hacked. This can also be the cause of hacking your account in the past, in the consequences may fall back in the future!
Here are the steps that were used:
- Know the e-mail address of the person.
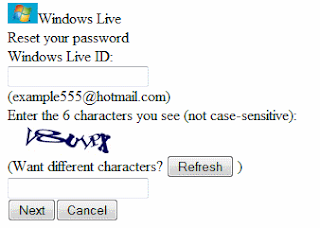
- Access the password reset page on the mobile version of the site (which at that time was security conscious).
- Enter the address of the target as well as the security captcha.
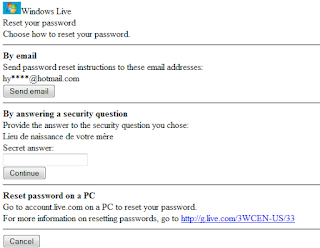
- A page was displayed asking to enter the secret question or to send the restore instructions to the backup address. This backup address is displayed according to the following model: ou******@hotmail.com.
- It was therefore necessary to start by finding this address partly hidden. And the flaw was at this level , indeed it was enough to display the source code of the page (CTRL + U under most browsers). And in the source code a value of type hidden was found there or the address appeared in clear, without the stars.
- This step required a lot of luck, it was necessary to check if this address of relief was used or not. The hacker went to the registration page HERE and registered with this address of relief.
- This address is often noted at the pif by people because it is mandatory at registration. Thus, an address put at random is very likely to be unused and it was enough for the pirate to appropriate the secondary account.
Once the hacker had managed to create this secondary account, he clicked on "Send email" and he received all instructions to reset the password of the account he wanted to hack. As simple as that, no programming knowledge required, no need to be a computer engineer, no need to use specialized tools!
Another way to hack a Hotmail account was to wait for the address to be several years old without being used. Hotmail accounts were automatically deleted when they were several years old ! It was therefore possible to hack any account , it was enough that the original owner logs in not for a while.
You'll understand: to hack your Hotmail account the hacker had to wait ...
Conclusion on this flaw and prevention methods
It only took a bit of cunning to test the mobile version and take a look at the source code of the page to find this trick more than formidable.
You now know that you have to pay attention to the backup address of an account, it is as importantas the main address. Also be aware that not logging in for a long time makes your account reusable by anyone else .
How not to be hacked in the future
Never give YOUR own credentials (e-mail addresses and password) to certain websites or programs. If you were actively looking for hacking a hotmail account before coming here you probably came across "specialized sites" and others "give me your IDs, I'll do it in 2 seconds". That's not true, be suspicious !
Now, we will see other hacking opportunities that are not technical this time and against which you must be protected .
Pay attention to keyloggers , who recover purely and directly your passwords
You tell yourself that outlook.com is http s , you use a proxy or VPN and nobody could thus steal your password.
FALSE.
Keyloggers get what you type on your keyboard, no matter the active window, no matter what the encryption of the connection is.
Pay attention to Phishing , which makes you believe that you are addressing an official website
With keyloggers, phishing is one of the most popular attacks to hack into any account. It's simple, you are made to believe that your information is not up to date (or any other technique in this genre) to send you to a fake site that retrieves your password . Phishing software also exists, typically with programs that require you to log in to perform an action while they recover your password.
Be careful to have a valid backup address , not unused or non-existent
Outlook / Hotmail requires to choose at least two identifiers, but for many users, this information is useless, so they fill an address of emergency, the pif!
It's just like sending your password to someone at random. It is also possible for anyone to create this address, which did not necessarily exist before.
Be careful to choose a complicated answer to the security question
In the same vein, users think they never need to use a secret answer, so they give it to the ghost(and do not remember when their account is hacked) or normally answer the question, which seems to be a good thing. But it is not at all , ask directly an individual "What was your first animal? Is enough to get the answer you are looking for is to hack an account!)
Be careful not to show the contents of your inbox and your account information
Seeing e-mails at work or at school seems harmless. But if a bad-minded person takes note of what she sees, she can hack a hotmail account (or whatever). Because by using the recovery form, anyone can pretend to know you a lot of information about your account, and thus reset your account.
Securely secure your accounts upstream
Once you are hacked it is often too late. Think about two-step authentication, the password or emergency phone number, and most importantly: Be suspicious and aware.